Thousands of companies rely on CCNP to get successful in their business. Cisco CCNP updates itself consistently, so professionals also need to adapt themselves accordingly. We provide Cisco https://www.pass4itsure.com/300-101.html dumps to prepare for Cisco CCNP exam in one go, instead of getting stuck for years.
Exam Code: 300-101
Exam Name: Implementing Cisco IP Routing (ROUTE v2.0)
Updated: Jul 17, 2017
Q&As: 402
Q: What was your favorite exam to create?
SNMPv3 by far – I set a personal goal to record as much information in 10 minutes as possible…this nugget is faster, funnier, and more packed with information than anything I’ve ever recorded before.
Q: What’s one real-world application someone can expect to use, thanks to this Cisco 300-101 dumps course?
Configuring multi-site, worldwide routing over an MPLS full-mesh cloud while tying in an Internet connection via BGP all while eating a tasty can of pizza flavored Pringles potato chips. Yum.

Free Pass4itsure Cisco 300-101 Dumps Exam Questions and Answers:
QUESTION NO: 32
Which GSC describes the degree to which the application communicates directly with the
processor?
A. Data communications
B. Distributed data processing
C. Transaction rate
D. Online update
300-101 exam Answer: A
QUESTION NO: 33
Which of the following statements is a characteristic of the GSC – complex processing?
A. Development of the application is influenced by how the development was carried out
B. Development of the application is influenced by the complexity of data communication
C. Development of the application is influenced by the complexity of the processing logic
D. None of the above
Answer: C
QUESTION NO: 34
Which transactional function(s) has (have) the primary intent of presenting information to the user
and must reference a data function to retrieve data or control information?
A. EI
B. EO
C. EQ
D. Both B and C
300-101 dumps Answer: C
QUESTION NO: 35
The primary intent of an EQ is to:
A. alter the behavior of the application
B. maintain one or more ILFs
C. present information to a user
D. Both A and C
Answer: C
QUESTION NO: 36
An External Inquiry is defined as an elementary process that:
A. Sends data outside the boundary
B. Sends Control Information outside the boundary
C. Has a primary intent to present information to a user through retrieval of data or control
information
D. All of the above
300-101 pdf Answer: D
QUESTION NO: 37
Which statement(s) is (are) true regarding mandatory processing logic for an EQ?
A. Data or control information is maintained
B. Conditions are analyzed to determine which are applicable
C. At least one ILF or EIF is referenced
D. Data or control information entering the boundary of the application is accepted
Answer: C
QUESTION NO: 38
Which processing logic can be performed by an EQ?
A. Equivalent values are converted
B. Behavior of the application is altered
C. Derived data is created
D. Both A and B
300-101 vce Answer: A
QUESTION NO: 39
The functional complexity of an EQ is based upon the number of:
A. RETs
B. FTRs
C. DETs
D. Both B and C
Answer: D
QUESTION NO: 40
Which of the following forms of processing logic is mandatory that an EO perform at least one
(m*)?
A. Behavior of the application is altered
B. Equivalent values are converted
C. At least one ILF or EIF is referenced
D. Information is prepared and then presented outside the boundary
300-101 dumps Answer: A
QUESTION NO: 41
Which of the following statements is true regarding EOs?
A. An EO is an elementary process that sends data or control information outside the boundary.
B. An EO includes additional processing logic beyond that of an EQ.
C. An EO always maintains a data function.
D. Both A and B
Answer: D
QUESTION NO: 42
Processing logic is defined as any of the requirements specifically requested by the user to
complete an elementary process. Those requirements include which of the following actions?
A. Validations
B. Algorithms or calculations
C. Reading or maintaining a data function
D. All of the above
300-101 exam Answer: D
QUESTION NO: 43
An External Output is defined as an elementary process that:
A. Includes addition processing beyond an external inquiry
B. Sends data outside the boundary
C. Has a primary intent to present information to a user though processing logic or in addition to
retrieval of data or control information.
D. All of the above
Answer: D
QUESTION NO: 44
Which of the following statements about an External Output are true?
A. Processing logic must contain multiple mathematical formulas
B. Processing logic must perform at least one mathematical formula
C. Processing logic creates derived data
D. Processing logic contains derived data
300-101 pdf Answer: C
QUESTION NO: 45
An FTR is be defined as a:
A. data function maintained by a base functional component
B. data function read and/or maintained by a transactional function
C. base functional component maintained by a transactional function
D. base functional component read and/or maintained by a transactional function
Answer: B
QUESTION NO: 46
What is the primary intent of an ILF?
A. Hold data maintained through system tools for use by the application being measured
B. Hold code data for use by the application being measured
C. Hold data maintained through one or more elementary processes of the application being
measured
D. Both A and C
300-101 vce Answer: C
QUESTION NO: 47
Data Element Type is defined as?
A. Functionality provided to the user to meet internal or external data storage requirements
B. An attribute that further describes one or more attributes of another entity
C. Two types of the base functional components identified in the IFPUG International Standard
D. Unique, user recognizable, non-repeated attribute
Answer: D
Students mostly use video tutoring and study guides while preparing for Pass4itsure 300-101 dumps for CCNP. Long Study guides often become very boring, making students tired. Whereas some students prefer video tutorials as they are less annoying. But, our study guides, and PDF materials are so simple, and to the point, and hardly would anyone feel frustrated, be it CCNP or something else.
In the new version of Pass4itsure https://www.pass4itsure.com/300-101.html dumps CCNP Routing and Switching, Cisco requires candidates to be proficient in StackWise and Virtual Switching Service (VSS) technologies. Both are used to make multiple physical switches behave like a single switch, but there are a number of design considerations and implementation details that impact their behavior in production networks from google drive: https://drive.google.com/open?id=0BwxjZr-ZDwwWWDdYaFM0SVFwMTA
Pass4itsure ICND2 https://www.pass4itsure.com/200-105.html dumps presents you with an organized test preparation routine through the use of proven series elements and techniques. “Do I Know This Already?” quizzes open each chapter and enable you to decide how much time you need to spend on each section. 200-105 exam topic lists make referencing easy.
Exam Code: 200-105
Exam Name: Interconnecting Cisco Networking Devices Part 2 (ICND2 v3.0)
Updated: Jul 16, 2017
Q&As: 204
Study Material for Cisco 200-105 Dumps ICND2 Outline
- Cisco Device Management
- Troubleshooting Networks
- Network Addressing
- VLANs and Trunking
- Spanning Tree Protocol
- Advanced Switch Redundancy
- Access Layer Security
- Routing Fundamentals
- EIGRP Configuration
- OSPF Configuration
- PPP WANs
- eBGP Configuration
- Secure VPNs and Tunneling
- Intelligent Networks
- Quality of Service

Free Pass4itsure Cisco 200-105 Dumps Exam Questions and Answers:
QUESTION 7
A network administrator has configured access list 173 to prevent Telnet and ICMP traffic from reaching a
server with the address of 192.168.13.26. Which commands can the administrator issue to verify that the
access list is working properly? (Choose three.)
A. Router# ping 192.168.13.26
B. Router# debug access-list 173
C. Router# show open ports 192.168.13.26
D. Router# show access-lists
E. Router# show ip interface
200-105 exam Correct Answer: ADE
QUESTION 8
DRAG DROP
Select and Place:
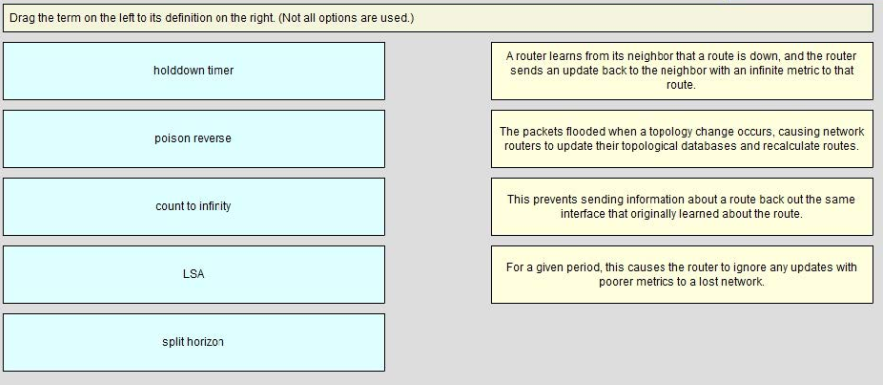
Correct Answer:
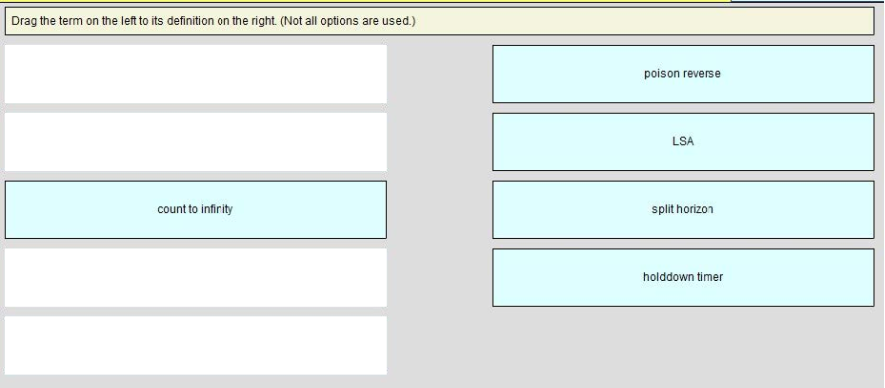
QUESTION 9
Lab – Access List Simulation
A network associate is adding security to the configuration of the Corp1 router. The user on host C should
be able to use a web browser to access financial information from the Finance Web Server. No other hosts
from the LAN nor the Core should be able to use a web browser to access this server. Since there are
multiple resources for the corporation at this location including other resources on the Finance Web
Server, all other traffic should be allowed.
The task is to create and apply a numbered access-list with no more than three statements that will allow
ONLY host C web access to the Finance Web Server. No other hosts will have web access to the Finance
Web Server. All other traffic is permitted.
Access to the router CLI can be gained by clicking on the appropriate host.
All passwords have been temporarily set to “cisco”.
The Core connection uses an IP address of 198.18.196.65
The computers in the Hosts LAN have been assigned addresses of 192.168.33.1 – 92.168.33.254
Host A 192.168.33.1
Host B 192.168.33.2
Host C 192.168.33.3
Host D 192.168.33.4
The servers in the Server LAN have been assigned addresses of 172.22.242.17 – 172.22.242.30
The Finance Web Server is assigned an IP address of 172.22.242.23.
The Public Web Server is assigned an IP address of 172.22.242.17
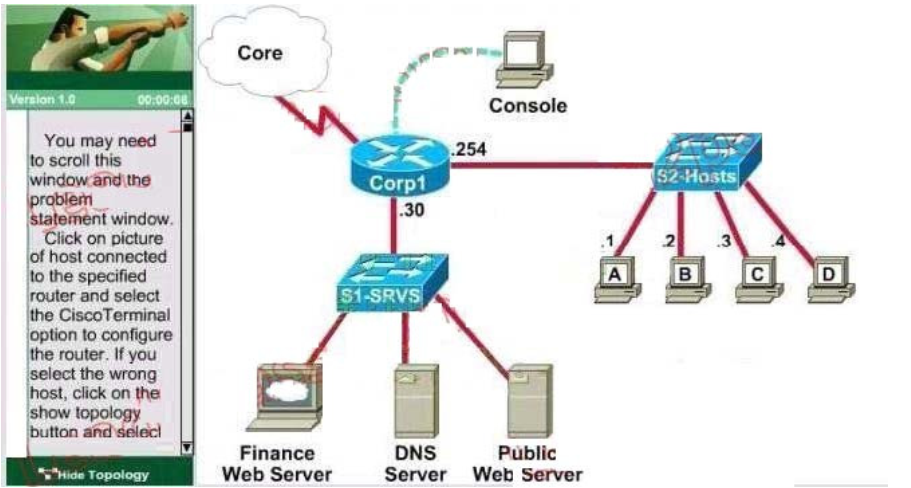
200-105 dumps Correct Answer: Check the answer in explanation
QUESTION 10
A sporting goods manufacturer has decided to network three (3) locations to improve efficiency in inventory
control. The routers have been named to reflect the location: Boston, Frankfurt, and Lancaster.
The necessary networking has been completed at each location, and the routers have been configured
with single area OSPF as the routing protocol. The Boston router was recently installed but connectivity is
not complete because of incomplete routing tables.
Identify and correct any problem you see in the configuration.
Note: The OSPF process must be configured to allow interfaces in specific subnets to participate in the
routing process.
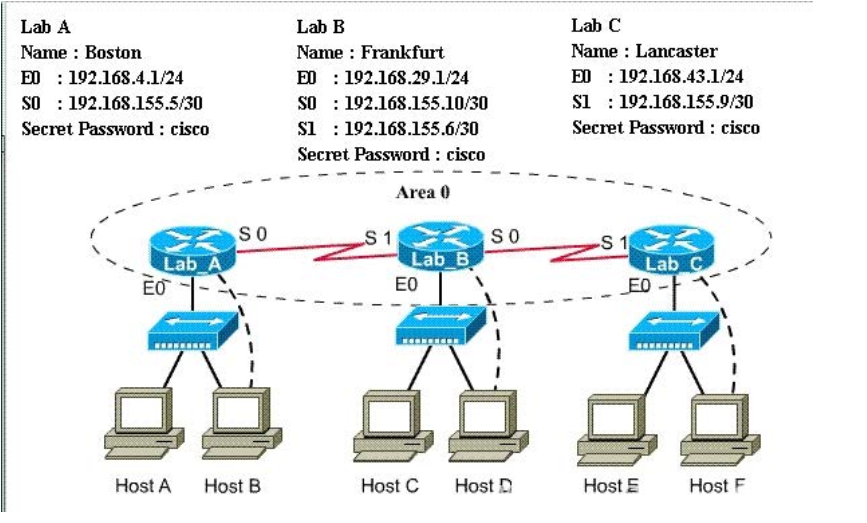
Correct Answer: The question mentioned Boston router was not configured correctly or incomplete so we
should check this router first. Click on Host B to access the command line interface (CLI) of Boston router.
QUESTION 11
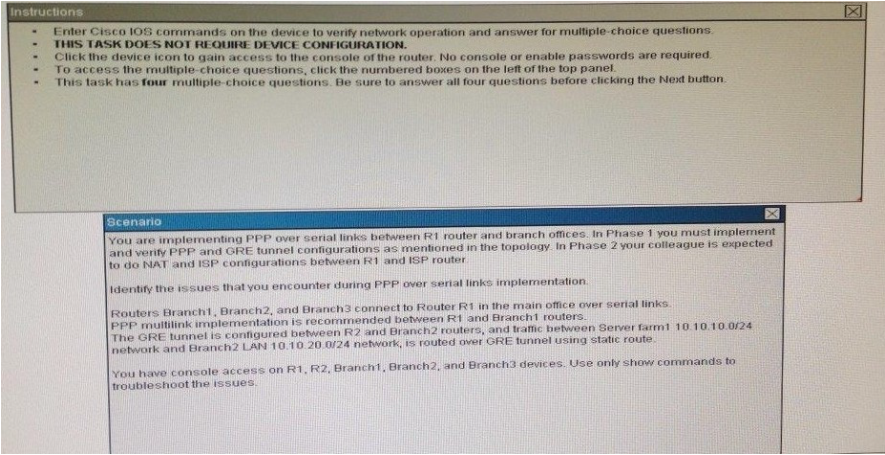
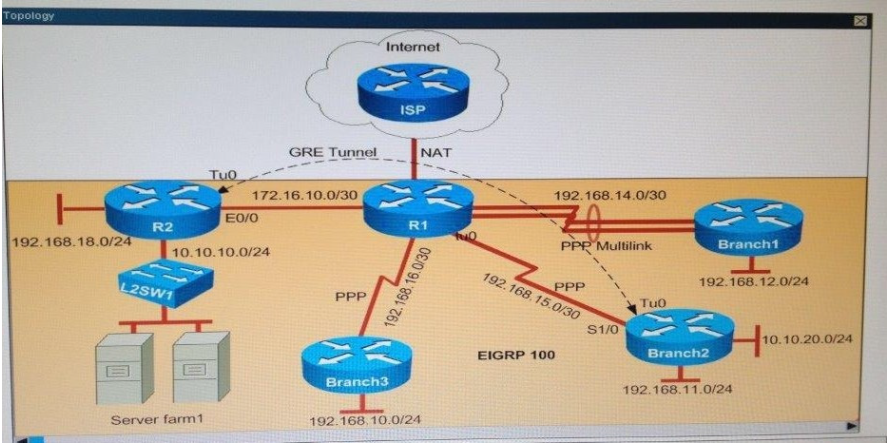
Why did Branch1 router lose WAN connectivity with R1 router?
A. The IP address is misconfigured on PPP multilink interface on the Branch1 router.
B. The PPP multilink group is misconfigured on the anch1 serial interfaces.
C. The PPP multilink group is misconfigured on the R1 serial interfaces.
D. The Branch1 serial interfaces are placed in a shutdown condition.
200-105 pdf Correct Answer: A
QUESTION 12
Which component of the Cisco SDN solution serves as the centralized management system?
A. Cisco OpenDaylight
B. Cisco ACI
C. Cisco APIC
D. Cisco IWAN
Correct Answer: B
QUESTION 13
Which EIGRP for IPv6 command can you enter to view the link-local addresses of the neighbors of a
device?
A. show ipv6 eigrp 20 interfaces
B. show ipv6 route eigrp
C. show ipv6 eigrp neighbors
D. show ip eigrp traffic
200-105 vce Correct Answer: C
QUESTION 14
What is a difference between TACACS+ and RADIUS in AAA?
A. Only TACACS+ allows for separate authentication.
B. Only RADIUS encrypts the entire access-request packet.
C. Only RADIUS uses TCP.
D. Only TACACS+ couples authentication and authorization.
Correct Answer: A
QUESTION 15
Which IEEE standard does PVST+ use to tunnel information?
A. 802.1x
B. 802 1q
C. 802.1w
D. 802.1s
200-105 dumps Correct Answer: B
QUESTION 16
Which type of interface can negotiate an IP address for a PPPoE client?
A. Ethernet
B. dialer
C. serial
D. Frame Relay
Correct Answer: B
QUESTION 17
Which statement about QoS default behavior is true?
A. Ports are untrusted by default.
B. VoIP traffic is passed without being tagged.
C. Video traffic is passed with a well-known DSCP value of 46.
D. Packets are classified internally with an environment.
E. Packets that arrive with a tag are untagged at the edge of an administrative domain.
200-105 exam Correct Answer: E
QUESTION 18
Refer to the exhibit.
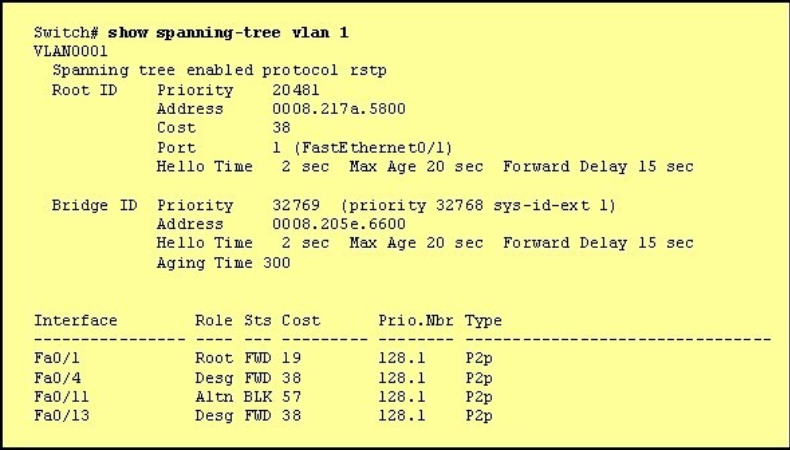
Why has this switch not been elected the root bridge for VLAN1?
A. It has more than one interface that is connected to the root network segment.
B. It is running RSTP while the elected root bridge is running 802.1d spanning tree.
C. It has a higher MAC address than the elected root bridge.
D. It has a higher bridge ID than the elected root bridge.
Correct Answer: D
QUESTION 19
Refer to the exhibit.
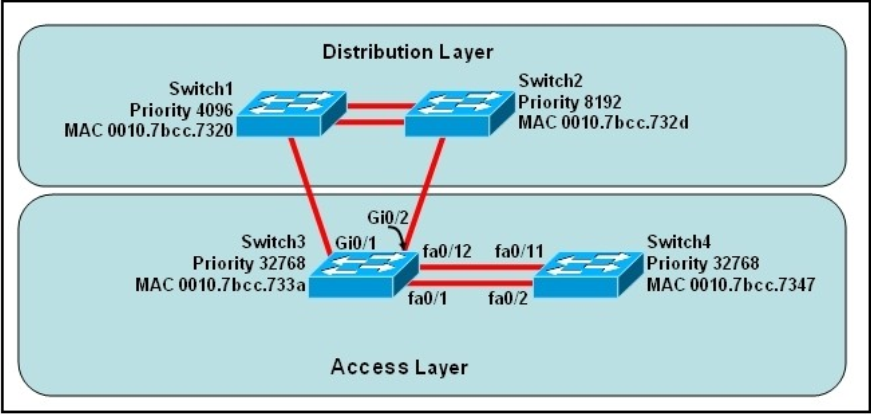
At the end of an RSTP election process, which access layer switch port will assume the discarding role?
A. Switch3, port fa0/1
B. Switch3, port fa0/12
C. Switch4, port fa0/11
D. Switch4, port fa0/2
E. Switch3, port Gi0/1
F. Switch3, port Gi0/2
200-105 pdf Correct Answer: C
QUESTION 20
Refer to the exhibit.
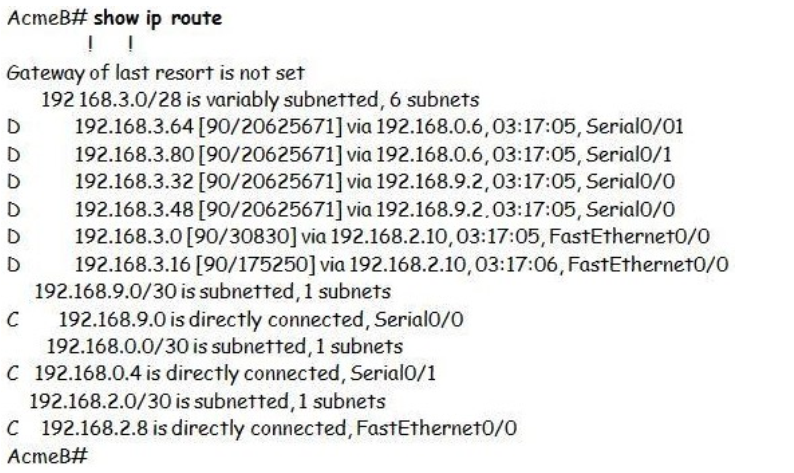
A packet with a source IP address of 192.168.2.4 and a destination IP address of 10.1.1.4 arrives at the
AcmeB router. What action does the router take?
A. forwards the received packet out the Serial0/0 interface
B. forwards a packet containing an EIGRP advertisement out the Serial0/1 interface
C. forwards a packet containing an ICMP message out the FastEthemet0/0 interface
D. forwards a packet containing an ARP request out the FastEthemet0/1 interface
Correct Answer: C
QUESTION 21
Which type of EIGRP route entry describes a feasible successor?
A. a backup route, stored in the routing table
B. a primary route, stored in the routing table
C. a backup route, stored in the topology table
D. a primary route, stored in the topology table
200-105 vce Correct Answer: C
QUESTION 22
What can be done to secure the virtual terminal interfaces on a router? (Choose two.)
A. Administratively shut down the interface.
B. Physically secure the interface.
C. Create an access list and apply it to the virtual terminal interfaces with the access-group command.
D. Configure a virtual terminal password and login process.
E. Enter an access list and apply it to the virtual terminal interfaces using the access-class command.
Correct Answer: DE
Now the 200-105 new questions arises how to go through Pass4itsure 200-105 dumps certification. The answer is so simple do preparation for Interconnecting Cisco Networking Devices Part 2 (ICND2 v3.0) exam. Our Cisco 200-105 dumps sample questions and ICND2 dumps have designed CCNA Routing and Switching 200-105 practice test preparation materials in order to solve the problems for Pass4itsure https://www.pass4itsure.com/200-105.html dumps ICND2.
Related More Cisco 200-105 pdf google drive:https://drive.google.com/open?id=0BwxjZr-ZDwwWWWw0QXQxY3R1X1E
70–767 pdf online learning is itself a benefit for learners. It facilitates them in certain number of fields. It has a lot of positive aspects for those who require more betterment in their lives. Learning Microsoft https://www.pass4itsure.com/70-767.html pdf practice test online can be discussed in many ways. Getting the 70–767 pdf for preparing the Microsoft Implementing an SQL Data Warehouse exam is the best option for the candidates.
Exam Code: 70-767
Exam Name: Implementing a SQL Data Warehouse (beta)
Updated: Jul 16, 2017
Q&As: 112
- Complete collection of 70-767’s pdf most related Question and answers
- Our 70-767 pdf study material meets with the exact
- Immediate access to 70-767 pdf questions and answers after buying
- Check out our 70-767 sample in a new PDF format:https://www.pass4itsure.com/
- 24×7 online support facility
Free Pass4itsure Microsoft 70-676 PDF Exam Questions and Answers:
Question: 69
This Security Standard addresses the proper functions to be performed on a specific workstation as
well as the physical attributes of its surroundings,
A. information Access Management
B. Workstation Security
C. Access Control
D. Facility Access Controls
E. Workstation Use
70-767 pdf Answer: E
Question: 70
In addition to code sets, HIPAA transactions also contain:
A. Security information such as a fingerprint.
B. Privacy information.
C. Information on all business associates,
D. Information on all health care clearinghouses.
E. Identifiers.
Answer: E
Question: 71
Select the correct statement regarding the administrative requirements of The HIPAA privacy rule.
A. A covered entity must designate, and document, a privacy official, security officer and a HIPAA
compliance officer
B. A covered entity must designate, and document, the same person to be both privacy official and
as the contact person responsible for receiving complaints and providing further information about
the notice required by the regulations.
C. A covered entity must implement and maintain written or electronic policies and procedures with
respect to PHI that are designed to comply with HIPAA standards, implementation specifications and
other requirements.
D. A covered entity must train, and document the training of. at least one member of its workforce
on the policies and procedures with regard to PHI as necessary and appropriate for them to carry
out their function within the covered entity no later than the privacy rule compliance date.
E. A covered entity must retain the document required by the regulations for a period often years
from the time of it’s creation or the time it was last in effect, which ever is later
70-767 vce Answer: C
Question: 72
To comply with the Privacy Rule, a valid Notice of Privacy Practices:
A. Is required for all Chain of Trust Agreements.
B. Must allow for the patient’s written acknowledgement of receipt.
C. Must always be signed by the patient.
D. Must be signed in order for the patient’s name to be sold to a mailing list organization.
E. Is not required if an authorization is being developed.
Answer: B
Question: 73
Security to protect information assets is generally defined as having:
A. Controls
B. PRI
C. Biometrics
D. VPN technology
E. Host-based intrusion detection
70-767 dumps Answer: A
Question: 74
One characteristic of the Notice of Privacy Practices is:
A. It must be written in plain, simple language.
B. It must explicitly describe all uses of PHI.
C. A description about the usage of hidden security cameras for tracking patient movements for
implementing privacy.
D. A description of the duties of the individual.
E. A statement that the individual must abide by the terms of the Notice.
Answer: A
Question: 75
Select the FALSE statement regarding the transaction rule.
A. The Secretary is required by statue to impose penalties of at least $100 per violation on any
person or entity that fails to comply with a standard except that the total amount imposed on any
one person in each calendar year may not exceed $1 .000.000 for violations of one requirement.
B. Health plans are required to accept all standard transactions.
C. Health plans may not require providers to make changes or additions to standard transactions.
D. Health plans may not refuse or delay payment of standard transactions.
E. If additional information is added to a standard transaction it must not modify the definition,
condition, intent, or use of a data element.
70-767 exam Answer: A
Question: 76
Which of the following is primarily concerned with implementing security measures that are
sufficient to reduce risks and vulnerabilities to a reasonable and appropriate level.
A. Access Establishment and Modification
B. Isolating Health care clearinghouse Functions
C. Information System Activity Review
D. Risk Management
E. Risk Analysis
Answer: D
Question: 77
The applicable methods for HIPAA-related EDI transactions are:
A. Remote and enterprise.
B. Claim status and remittance advice.
C. Subscriber and payer.
D. Batch and real-time.
E. HCFA-1500 and 837.
Answer: D
Question: 78
A valid Notice of Privacy Practices must
A. Detail specifically all activities that are considered a use or disclosure
B. Describe in plain language what is meant by treatment, payment, and health care operations
(TPO).
C. Inform the individual that protected health information (PHI) may only be used for valid medical
research.
D. Inform the individual that this version of the Notice will always cover them, regardless of
subsequent changes.
E. State the expiration date of the Notice.
70-767 pdf Answer: B
Question: 79
The office manager of a small doctors office wants to donate several of their older workstations to
the local elementary school. Which Security Rule Standard addresses this situation?
A. Security Management Process
B. Device and Media Controls
C. information Access Management
D. Facility Access Controls
E. Workstation Security
Answer: B
Question: 80
Information in this transaction is generated by the payer’s adjudication system:
A. Eligibility (2701271)
B. Premium Payment 2O)
C. Unsolicited Claim Status (277)
D. Remittance Advice 35)
E. Functional Acknowledgment (997)
Answer: D
Question: 81
The key objective of a contingency plan is that the entity must establish and implement policies and
procedures to ensure The:
A. Creation and modification of health information during and after an emergency.
B. Integrity of health information during and after an emergency.
C. Accountability of health information during and after an emergency.
D. Vulnerability of health information during and after an emergency.
E. Non-repudiation of the entity.
70-767 vce Answer: B
Question: 82
A covered entity’ that fails to implement the HIPAA Privacy Rule would risk:
A. $50O0 in fines.
B. $5000 in fines and six months in prison.
C. An annual cap of $5000 in fines.
D. A fine of up to $50000 if they wrongfully disclose PHI.
E. Six months in prison.
Answer: D
Question: 83
This transaction supports multiple functions. These functions include: telling a bank to move money
OR telling a bank to move money while sending remittance information
A. 277.
B. 276
C. 271
D. 820.
E. 270.
70-767 dumps Answer: D
Question: 84
When PHI is sent or received over an electronic network there must be measures to guard against
unauthorized access. This is covered under which security rule standard?
A. Device and Media Controls
B. Access Controls
C. Transmission Security
D. Integrity
E. Audit Controls
Answer: C
Question: 85
Title 1 of the HIPAA legislation in the United States is about:
A. P1<1 requirements for hospitals and health care providers.
B. Encryption algorithms that must be supported by hospitals and health care providers.
C. Fraud and abuse in the health care system and ways to eliminate the same.
D. Guaranteed health insurance coverage to workers and their families when they change
employers.
E. The use of strong authentication technology that must be supported by hospitals and health care
providers.
Answer: D
Question: 86
Implementing policies and procedures to prevent, detect, contain, and correct security violations is
required by which security standard?
A. Security incident Procedures
B. Assigned Security Responsibility
C. Access control
D. Facility Access Controls
E. Security Management Process
Answer: E
Here, candidates can get Pass4itsure 70-767 pdf questions answers that are prepared by the expert faculty. This study guide is designed as per Implementing an SQL Data Warehouse test engine with free 70-767 dumps. Choose the most eligible site that offers the online services of for all type of Microsoft MCSA SQL 2016 70-767 practice exam and Microsoft 70-767 pdf test questions.
It is quite obvious that passing this Implementing an SQL Data Warehouse exam is not a simple piece of paper writing. It needs extreme expert choice along with great proficiency. Getting online help for prepared Microsoft MCSA https://www.pass4itsure.com/70-767.html pdf test is quite common these days. The Microsoft 70-767 pdf simulator and 70-767 exam dumps are easily available at their professional site from google drive: https://drive.google.com/open?id=0BwxjZr-ZDwwWaWpOOFpVd3ZyMTg
















